The latest release of the Binarly Transparency Platform introduces powerful new capabilities that bring clarity to the chaos of vulnerability management and software supply chain security. This update is purpose-built to help enterprise defenders to prioritize what truly matters and to surface the vulnerabilities that pose real, immediate security risk.
Packed with research-driven exploitation intelligence, improved detection coverage, and deeper supply chain visibility, the platform delivers a more focused, actionable experience. It’s everything you need to move faster, reduce noise, and respond confidently to what’s being exploited or escalated in real-time.
In previous releases of the Binarly Transparency Platform, we built a strong foundation that paved the way for the advancements introduced in v3.0. Each version delivered key capabilities to support deeper visibility, smarter prioritization, and team collaboration:
These milestones laid the groundwork for v3.0’s real-time prioritization and threat intelligence capabilities.
We built the Binarly Transparency Platform v3.0 with ambitious plans to focus on smarter prioritization and help our customers zero in on the issues that require urgent attention the most. The platform introduces threat intelligence–driven prioritization, where priority is no longer just syntactic or probabilistic.
Instead, it is prioritization defined by real-world signals whether from new threats or escalations tied to previously known vulnerabilities. This shift empowers teams to respond faster and more confidently to what’s actually being exploited, not just what might be.
Binarly customers are using the platform to easily surface important findings with elevated risk that demand immediate attention, or to define their own priority views to stay focused and seamlessly return to the security issues that matter most. Users have the flexibility to define their own prioritization strategies based on internal risk models or operational needs, or they can leverage Binarly’s curated policy templates designed to highlight the most critical threats based on real-world exploitation signals and industry best practices.

The new Threat Intelligence Monitoring feature in this release bridges the gap between vulnerability data and real-world exploitation signals, giving teams immediate insight into active threats as they unfold.
One of the core innovations in this release is the introduction of the Exploitation Maturity Score (EMS). EMS is designed to go beyond Exploit Prediction Scoring System (EPSS) by reducing reliance on probabilistic models and instead leveraging real-time exploitation signals through a transparent, weighted linear scoring approach.
The result is a more actionable, evidence-based view of vulnerability risk grounded in what’s actually happening, not just what might happen.
The Binarly REsearch team designed EMS not to predict the future, but to measure the present by using real-world signals like public PoCs, exploit reliability, ransomware activity, public and private threat intelligence telemetry.

The historical changes in EMS scores and threat intelligence signals are continuously tracked by the platform and visualized within the dashboard. This allows security teams to monitor how the exploitation maturity of individual findings evolves over time whether it’s the appearance of a new PoC, weaponized exploit, CISA KEV inclusion, or active threat escalation with ransomware groups.
With this historical context, teams gain a clearer understanding of how a vulnerability’s risk profile is trending, enabling more informed decisions and faster proactive response.

The Threat Intelligence Monitoring service is fully developed in-house by the Binarly team and backed by a rich collection of both public and select private data sources. Our dedicated Threat Intelligence team continuously monitors, curates, and updates these intelligence signals to ensure timely and relevant insights into emerging exploitation trends.
This feature was born directly from a request by one of our enterprise users looking for a faster, more reliable way to communicate vulnerability disclosures, especially when third-party code is involved, which often happens with our unknown (0-day) vulnerability discoveries.
With this release, when the platform discovers a new, unknown vulnerability, the user can automatically generate an actionable advisory to share with the affected vendor.

For known vulnerabilities, users can generate VEX (Vulnerability Exploitability eXchange) files to efficiently communicate status and impact across your software supply chain. This streamlines the coordination process and accelerates response or communication with your customers.

The Binarly Transparency Platform (BTP) has evolved into a powerful data platform over time. One of the most consistent pieces of feedback we’ve heard from customers and prospects is the need to navigate and explore data at a global level by making it easier to extract insights or quickly find what’s most relevant in the moment.
We took that feedback seriously, and with this release, we’re excited to introduce the first iteration of Global Search across the platform, giving users a smarter, faster way to discover what matters most across their entire software inventory.

As software supply chains grow more complex, the ability to instantly search across all products, components, vulnerabilities, and artifacts becomes essential. This feature transforms data navigation from a fragmented, manual process into a seamless, intelligent experience.
Whether you’re hunting for a specific CVE, analyzing third-party component usage, or tracking exposure across product lines, Global Search helps you find answers in seconds, not hours. It’s a critical step toward making large-scale security data more accessible, actionable, and aligned with how enterprise security teams operate.

Now you can easily export any grid view in CSV format, making it simple to share findings across teams or load them into your favorite spreadsheet tools for deeper analysis and reporting. Whether you’re preparing a risk review, sharing vulnerability data with engineering, or archiving your findings, CSV export gives you the flexibility to move seamlessly between the Binarly platform and your existing workflows.
In addition to enhanced data portability, we’re introducing two powerful new report types:
These reports help amplify the value of Binarly’s deep binary analysis by aligning your software artifacts with modern cryptographic standards and secure development practices. The Post-Quantum Compliance report evaluates readiness for emerging cryptographic transition and compliance to government mandates, while the Secure by Design report highlights systemic weaknesses and insecure coding patterns that could become future exploit vectors.

Together with the other reporting services within Binarly Transparency Platform, they offer a strategic lens on not just fixing today’s vulnerabilities, but building more resilient software for tomorrow.
The latest update to the Binarly Transparency Platform brings significant enhancements to our code analysis engine, driven by improvements to our internal framework and decompiler. These updates include smarter handling of stubs, fixups, and other low-level constructs that improve the accuracy and depth of analysis across complex software components. We’ve also enhanced reporting for unknown vulnerabilities by exposing clearer evidence paths including source, sink, and data flow elements to provide more context and confidence around each vulnerability or malicious code finding.
These advancements are part of Binarly REsearch's ongoing commitment to pushing the boundaries of binary analysis. Our team is constantly innovating to deliver state-of-the-art capabilities that uncover what others miss, helping customers stay ahead of the curve in a constantly evolving threat landscape.
Binarly is a uniquely positioned company where every new vulnerability checker added to the platform is rigorously tested against real-world firmware and software artifacts. Our research-driven methodology has led to the discovery and disclosure of numerous previously unknown vulnerabilities (0-days) across a wide range of device vendors and software ecosystems. By validating detection logic through real exploitation scenarios and deeply analyzing production-grade firmware, we ensure that each checker not only works in principle but delivers tangible security value to our customers.
The new unknown vulnerability checkers, powered by our Deep Vulnerability Analysis (DVA) technology, are specifically designed to enhance proactive detection of CWE-20 (Improper Input Validation) vulnerabilities within privileged UEFI code, particularly in critical areas like SMI handlers and other sensitive execution paths. These vulnerability checkers focus on insecure input data processing patterns that are often overlooked during traditional source code analysis flows.
In many real-world scenarios, these types of vulnerabilities can lead to memory corruption issues, allowing an attacker to write fixed or predictable data to an attacker-controlled memory address. Left unaddressed, such flaws open the door to persistent firmware-level attacks that can bypass operating system controls and compromise platform integrity at its core.

Code execution in System Management Mode (SMM) can bypass critical security protections enabling the installation of stealthy firmware implants or backdoors. Such implants are resilient, often persisting across operating system reinstallations. Moreover, this vulnerability could be leveraged to undermine key UEFI security mechanisms like Secure Boot and potentially bypass memory isolation and confidential computing features used by hypervisors, significantly expanding the attacker’s control.
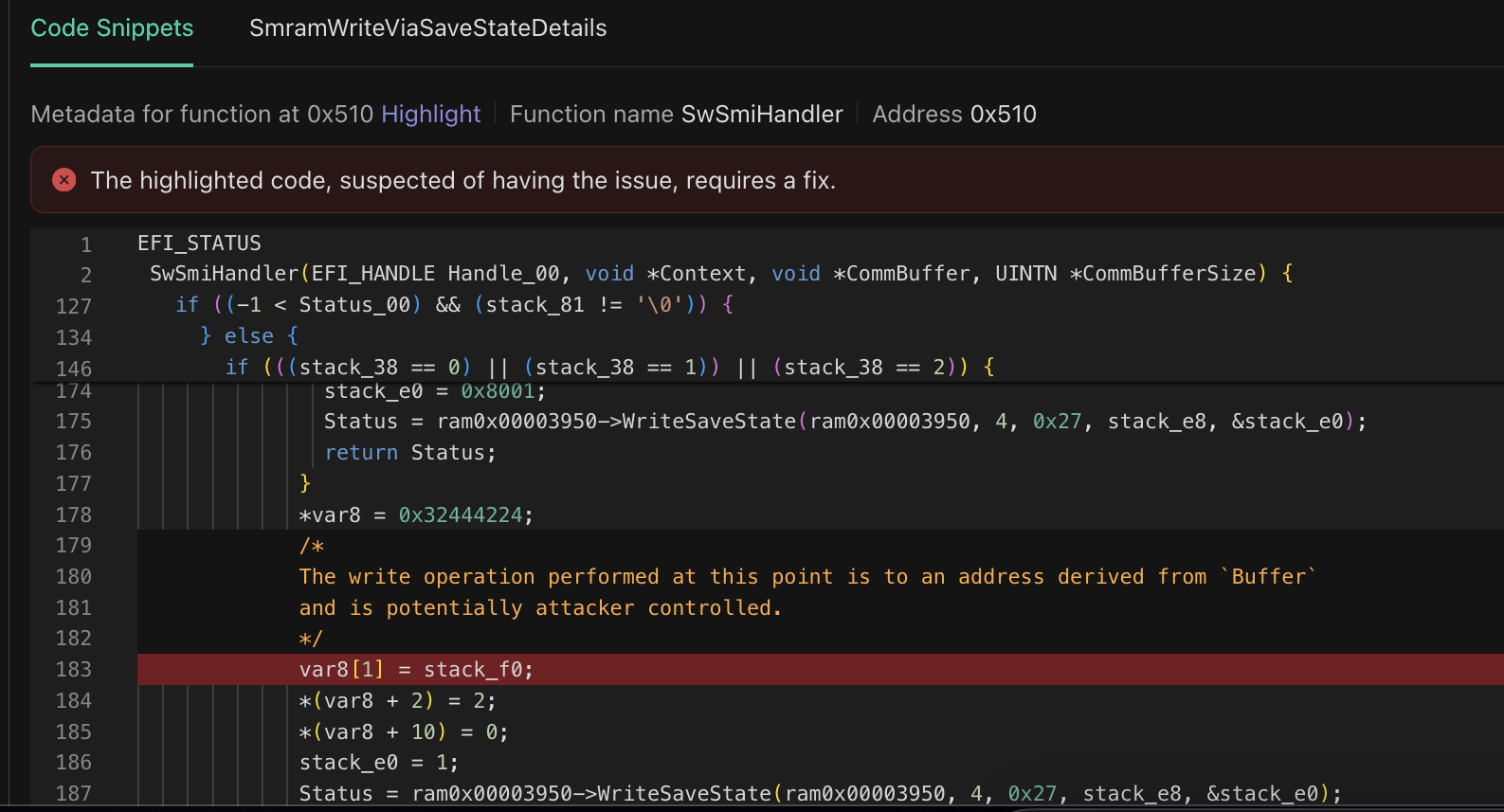
The new DVA-powered checkers have already uncovered and reported over 20 previously unknown, high-impact vulnerabilities, demonstrating their effectiveness in identifying critical flaws that traditional methods often miss.
As a direct result of our in-depth research into UEFI bootkits and unique code behaviors (outlined in our recent blog) we’ve developed a new set of checkers focused on detecting suspicious functionality in UEFI modules. These include detection of anomalies in PE parsing, import resolution, and relocation handling, which are often leveraged by stealthy threats attempting to hide below the OS. This release brings those research-driven insights directly into the Binarly Transparency Platform, giving defenders better tools to uncover advanced persistence techniques and harden firmware at scale.

The Binarly Transparency Platform has full support for scanning microcode embedded in UEFI firmware. By combining publicly available sources, vendor advisories, and a Binarly-maintained database of microcode revisions derived from ecosystem data, the platform can detect any security vulnerability related to microcode (like CVE-2024-56161) but also when firmware contains outdated microcode (more details in our blog).
.gif)
This update brings accurate detection of compiler versions, build ecosystems, and toolchain metadata, giving you deeper visibility into the origin and context of your software artifacts. By identifying the exact compiler and environment used during the build process, the platform can expose vulnerabilities and risks tied to specific toolchains, such as outdated compilers or ecosystem-specific flaws.
This enriched visibility also helps in tracing artifact provenance, validating SBOMs, and improving accountability across the software supply chain. It’s a critical step toward understanding not just what was built, but how it was built.

As part of our evolving extracted artifacts management capabilities, we now support the extraction and analysis of embedded cryptographic artifacts within software components. This enables security teams to identify and inventory cryptographic materials (such as certificates, keys, and signatures) directly from binaries.
By exposing these hidden assets, organizations gain better visibility into cryptographic hygiene, uncover potential misconfigurations or legacy algorithms, and strengthen their compliance with policies like post-quantum readiness and secure-by-design mandates.

Last but not least, our Enhanced Secret Detection feature now includes a built-in validation service to improve accuracy and reduce false positives. This means that when potential secrets (like API keys, tokens, or credentials) are detected within binaries, the platform can automatically validate them against known formats or live endpoints (where applicable).

This added layer of verification helps teams distinguish between actual exposures and benign patterns, streamlining triage and enabling faster, more confident responses to real risks embedded in your code or third-party components.

Looking ahead, our plan is to focus on closing the visibility gap in third-party components and open-source dependencies by making it easier to search, navigate, and understand risk across the entire software supply chain. We’ll continue advancing our prioritization engine to better serve both security and product teams, while evolving our threat intelligence based on customer feedback.
Binarly REsearch is also preparing groundbreaking innovations in custom semantic rule-based detection engine and the discovery of new classes of previously unknown (0-day) vulnerabilities.
Every release of the Binarly Transparency Platform raises the bar for the industry, as we remain committed to solving the software supply chain security puzzle: one signal, one breakthrough, and one release at a time.
Stay tuned! There’s much more to come 🚀✨